looking for Zero-trust-model-1.png - Microsoft 365 Blog you’ve visit to the right web. We have 35 Images about Zero-trust-model-1.png - Microsoft 365 Blog like Zero-trust-model-1.png - Microsoft 365 Blog, Pros And Cons Of The Zero Trust Model and also Secure Your Remote Workforce With Zero Trust Security | NCi Technologies. Here you go:
Zero-trust-model-1.png - Microsoft 365 Blog

Source: microsoft.com
.
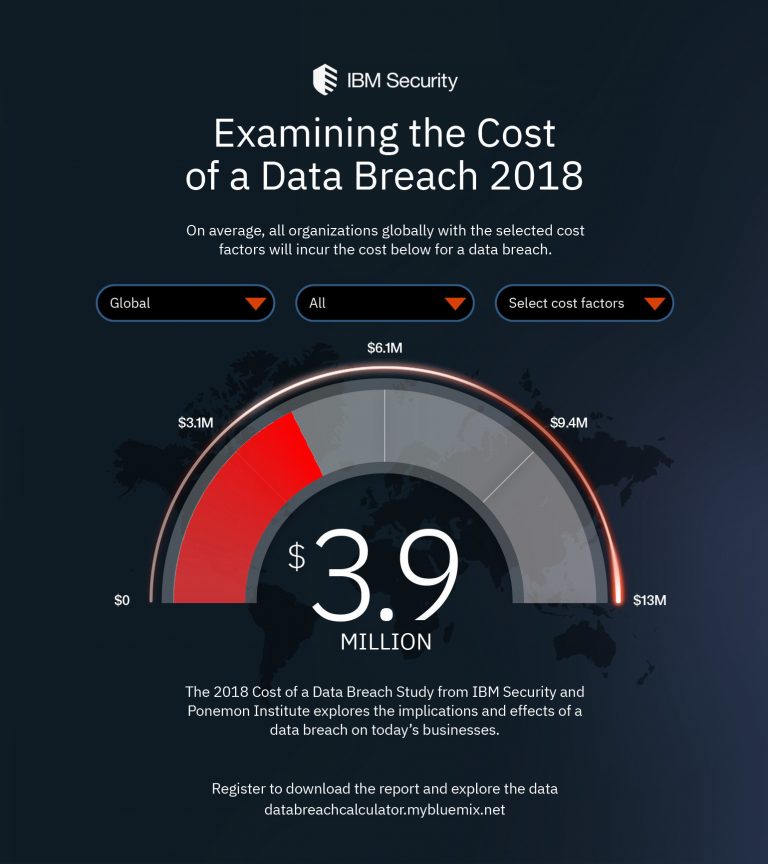
Download And Practice These Free COG-702 Braindumps.
Source: babelouedstory.com
.
Using Zero Trust To Protect Cellular IoT Devices - ZARIOT : ZARIOT

Source: zariot.com
iot cellular.
Quan điểm Của IBM CISO: Zero Trust Thay đổi Bảo Mật Từ Việc Bạn Làm

Source: vina-aspire.com
.
TEIMAS Platform ZERØ Solves Traceability Of Waste Using Blockchain

Source: eitrawmaterials.eu
.
Latest News

Source: iotforall.com
.
Zero Trust Architecture And Security Explained Papercut | My XXX Hot Girl
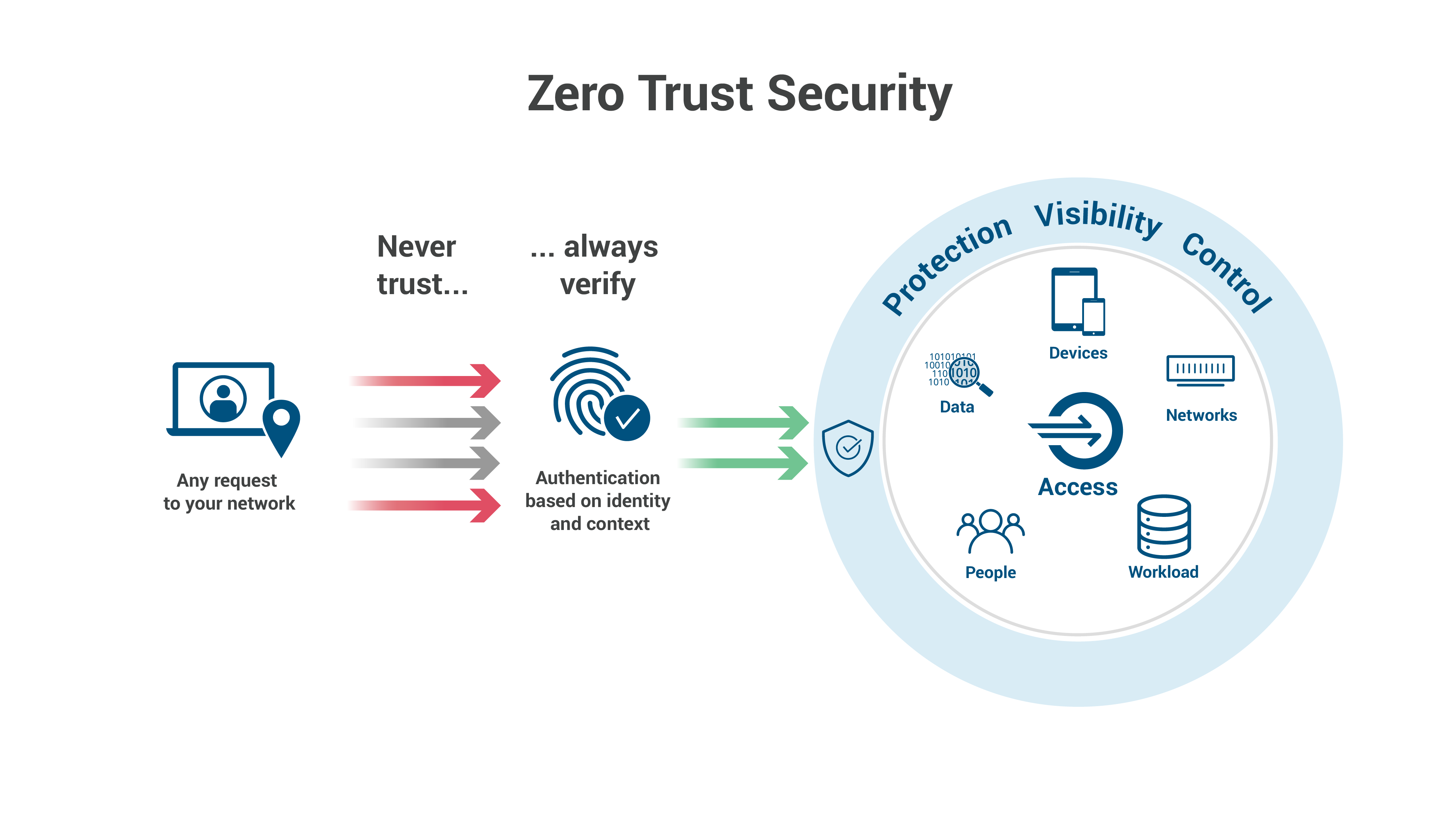
Source: myxxgirl.com
.
IoT And M2M Modules | Telit Cinterion

Source: telit.com
.
Products - Hyperthings - Building A Connected World With IOT - Products

Source: hyperthings.in
.
Telit DeviceWISE® CLOUD IoT Solution | Telit

Source: telit.com
.
Why Zero Trust Framework And What Is It

Source: neshacorp.com
trust microsoft identity implementing implementation architectuur devices.
Secure Your Remote Workforce With Zero Trust Security | NCi Technologies
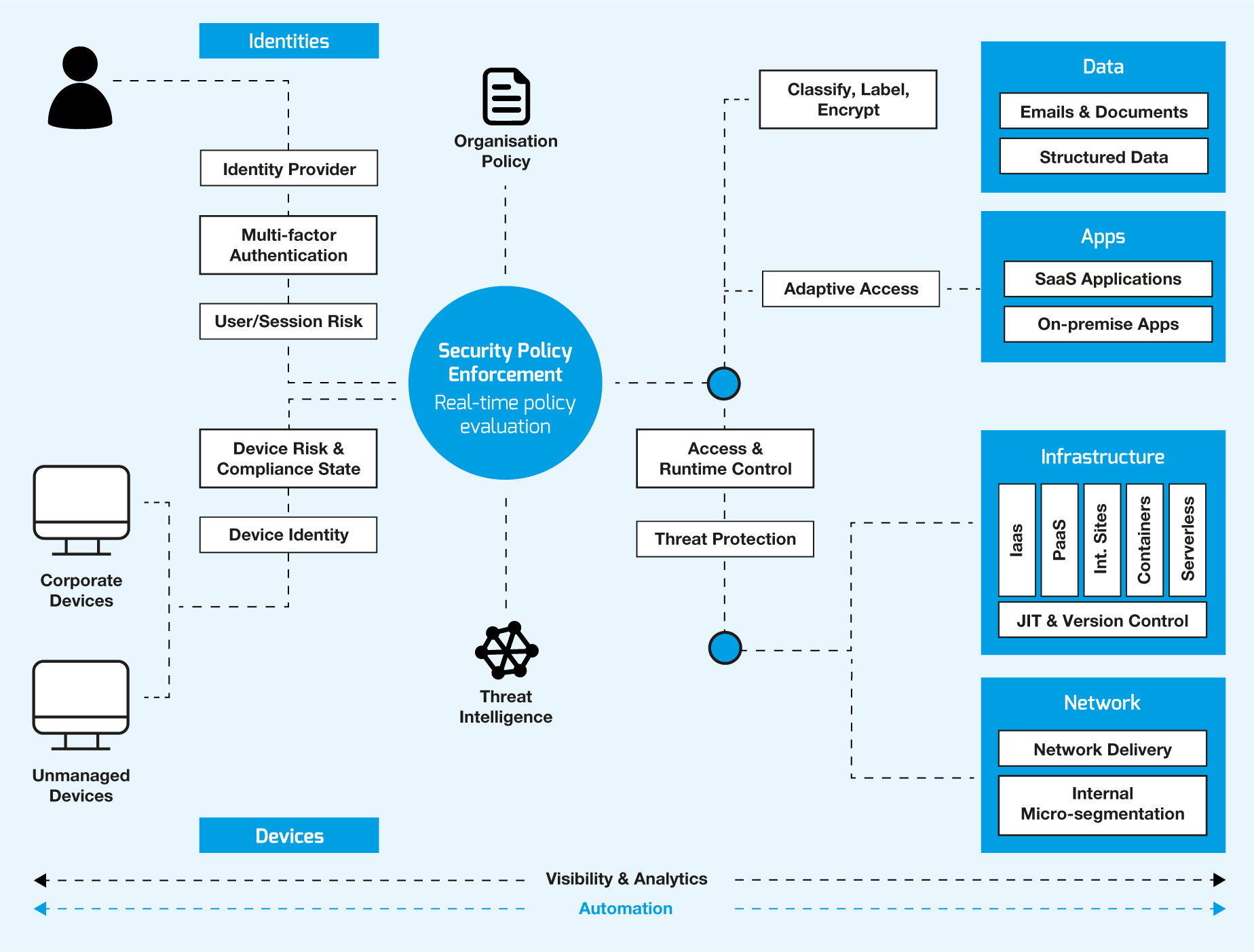
Source: ncitech.co.uk
trust pillars workforce.
The Top 10 Zero Trust Security Solutions | Expert Insights

Source: expertinsights.com
.
IoT Application Enablement And Device Management Platforms

Source: telit.com
.
Why Successful Digital Transformation Demands A Zero Trust Security

Source: onlinewhitepapers.com
.
IoT Application Enablement And Device Management Platforms

Source: telit.com
.
Zero Trust Security Explained | Zero Trust Components & Implementation
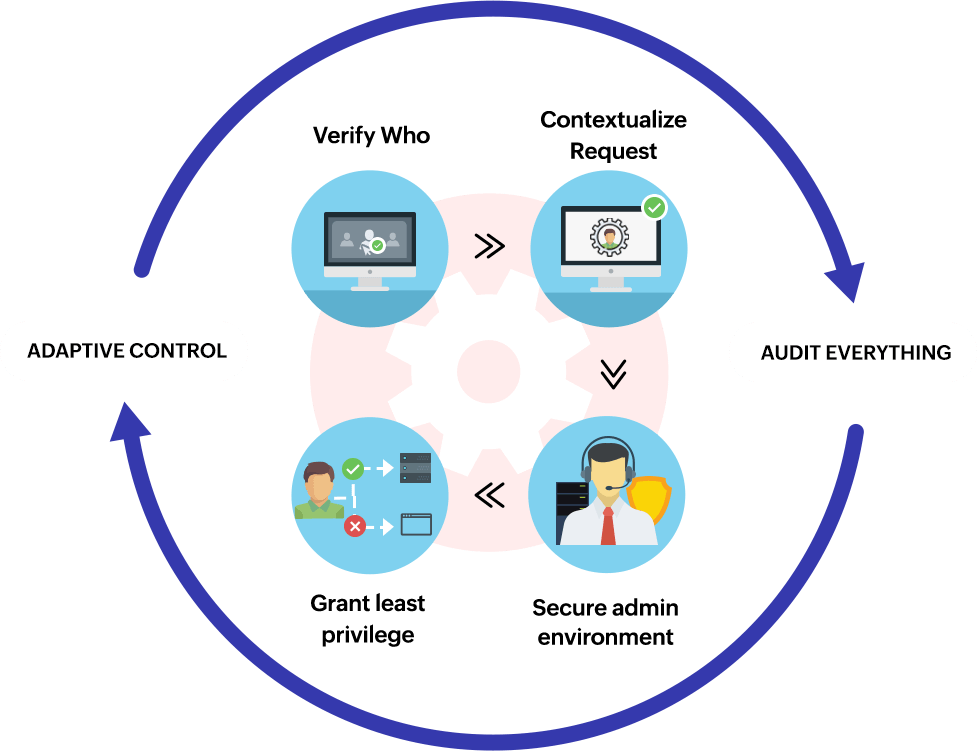
Source: manageengine.com
.
In-depth Guide To Zero Trust Paradigm & Zero Trust Architecture
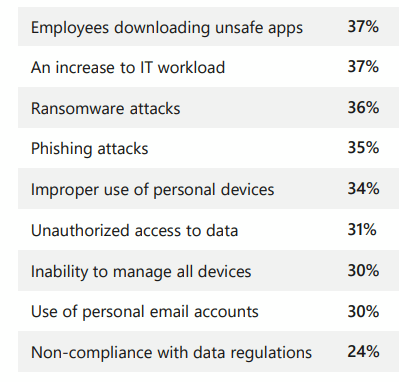
Source: research.aimultiple.com
.
What Is Zero Trust Model | Images And Photos Finder
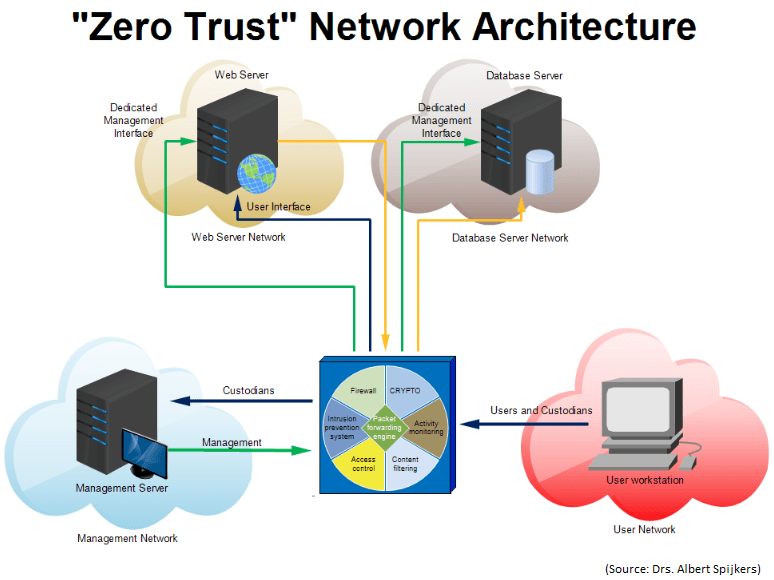
Source: aiophotoz.com
.
Why Zero Trust In IAM Is The New Way Forward - ManageEngine Blog

Source: blogs.manageengine.com
iam forward manageengine ad360.
How To Implement Zero Trust Security Model With Azure AD
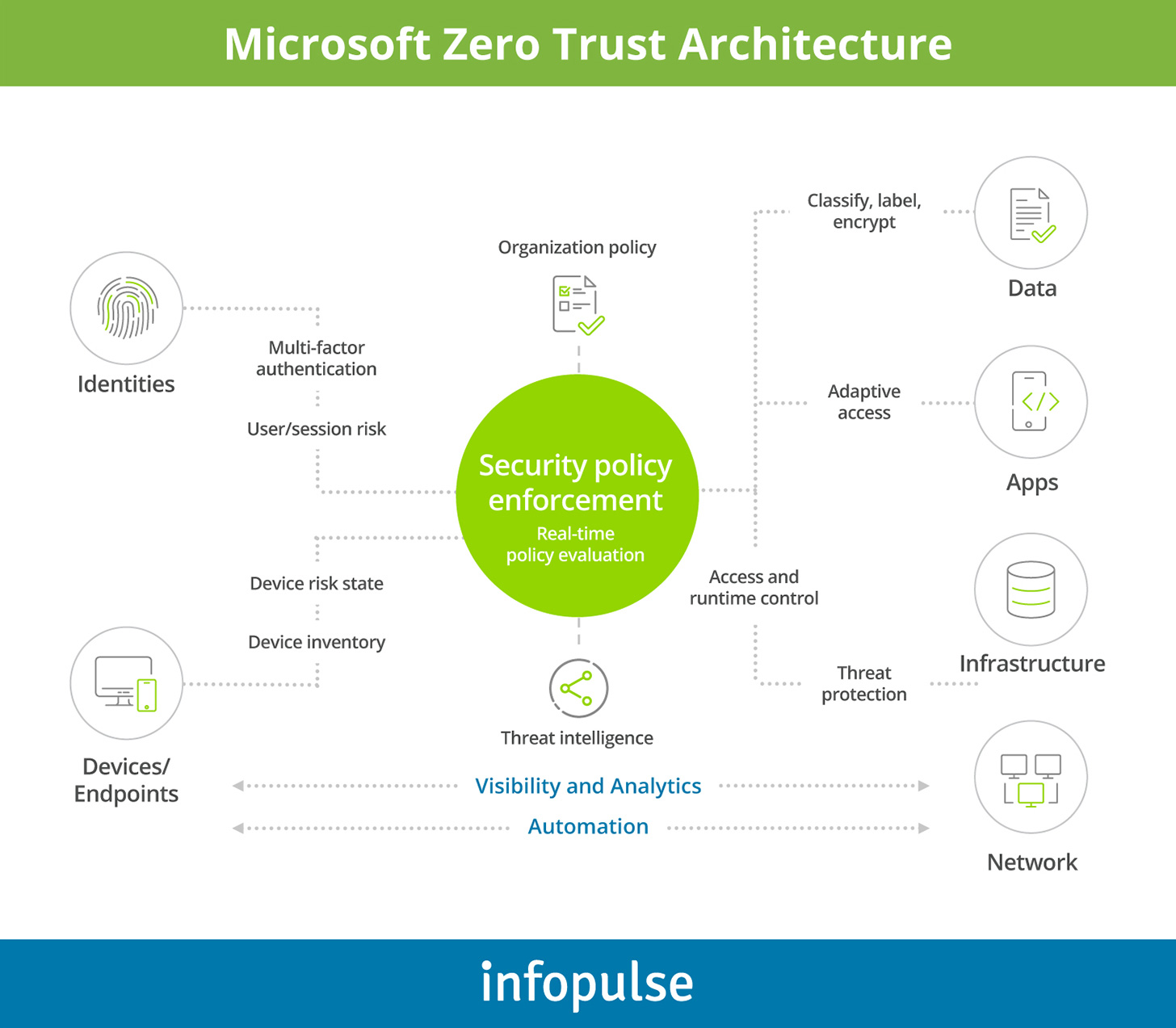
Source: infopulse.com
infopulse management.
Microsoft And Zscaler Help Organizations Implement The Zero Trust Model
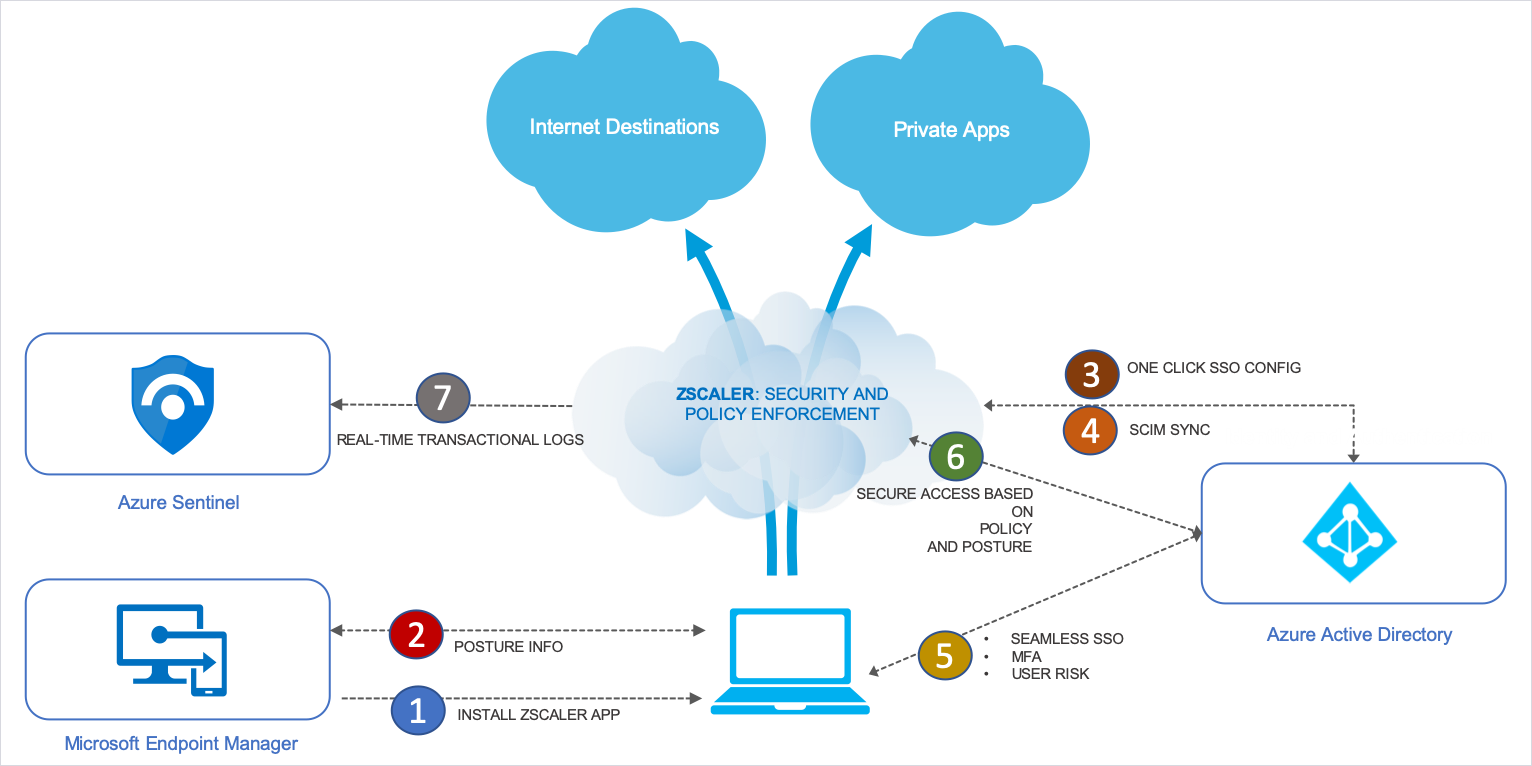
Source: threatshub.org
zscaler implement infographic sentinel secure securing threatshub cybersecurity directory endpoint manager enforcement.
Zero Trust Guide: Mobile Device Security

Source: blogs.blackberry.com
trust zero guide mobile device security blackberry blogs.
Implementing A Zero Trust Security Model At Microsoft
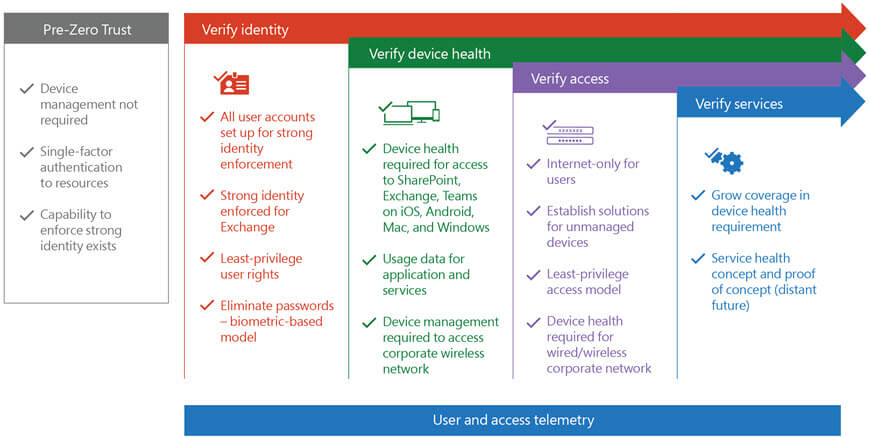
Source: microsoft.com
trust zero microsoft model security implementing implementation access phase performed components major each figure work diagram services identity data user.
Pros And Cons Of The Zero Trust Model
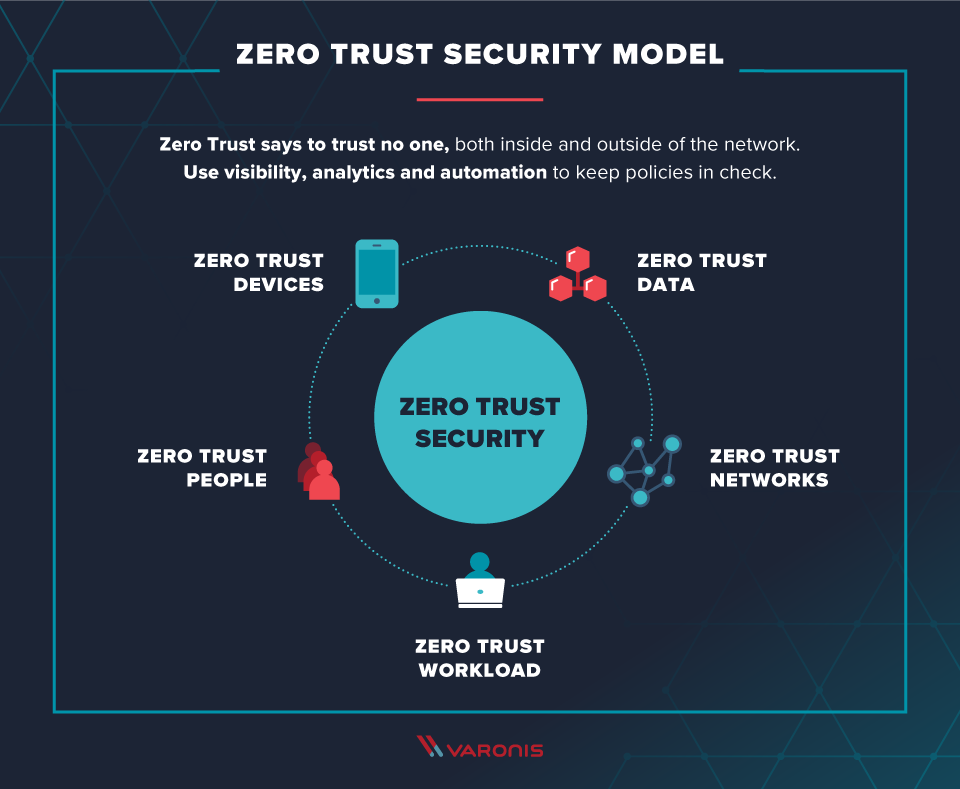
Source: infusedinnovations.com
trust cons.
How To Think About Zero Trust Architectures On AWS | AWS Public Sector Blog

Source: aws.amazon.com
aws architectures.
Using Zero Trust Principles To Protect Against Sophisticated Attacks

Source: microsoft.com
.
How Businesses Can Implement 'Zero Trust Security'?
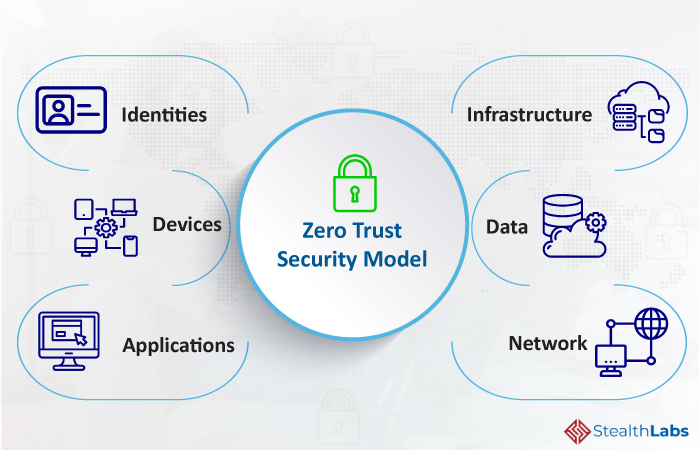
Source: stealthlabs.com
implement identities.
IoT Consulting - Hyperthings - Building A Connected World With IOT
Source: hyperthings.in
.
Digital Wellbeing Any Android Devices How To Use [HINDI] - YouTube
![Digital Wellbeing any android devices how to use [HINDI] - YouTube](https://i.ytimg.com/vi/b9D04oZvax8/maxresdefault.jpg)
Source: youtube.com
.
IoT And M2M Modules | Telit Cinterion

Source: telit.com
.
Digital Wellbeing 'Heads Up' Feature Reminds People To Stop Using Their
Source: beebom.com
.
Zero Trust Network Architecture Diagram
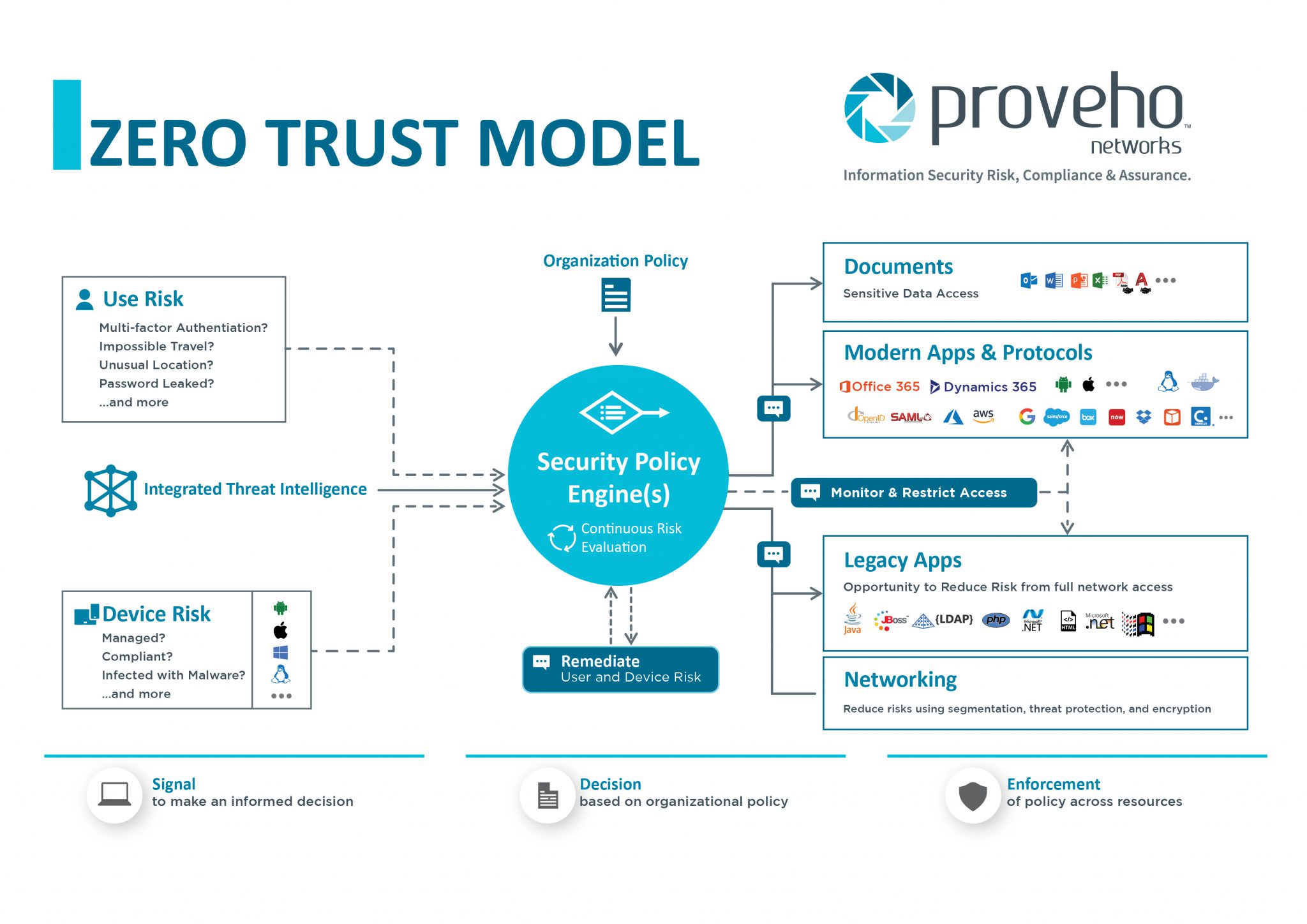
Source: mungfali.com
.
About Us - Hyperthings - Building A Connected World With IOT - About Us
Source: hyperthings.in
.
IoT And M2M Modules | Telit Cinterion

Source: telit.com
.